Introduction
The connected electronic information network has become an essential part of our daily lives. All types of organizations utilize the network by collecting, processing, storing and sharing vast amount of digital information. As more digital information is gathered and shared, the protection of this information and recognizing the potential vulnerabilities is becoming even more vital to our national security and economic stability. Identity theft is one of the most common cyber crimes in the internet that we should be aware as internet users.
Your Online & Offline Identity?
As more time is spent online, your identity on both online and offline can affect your life. Your “Offline Identity” is the person who your friends and family interact with on a daily basis at home, at school or work. They know your personal information such as name, age or where you live. Your “Online Identity” is how you present yourself to the others online. This online identity should only reveal a limited amount of information about you.
Identity theft is the deliberate usage of someone else’s identity in the internet, in order to gain a financial advantage or obtain credit and other benefits. Nowadays, it has become a common practice to use their true identity. Identity theft is not a new phenomenon; this term was coined in 1964. It has been used and continues to be used in the frame of social security fraud, bank loan fraud, assurance fraud etc.Your personal information is a goldmine for cyber thieves.ex: Name, Email Address, Phone Numbers, Banking Details, Medical Records.They will attempt to steal information and then use it for fraudulent activities and other crimes such as selling information.
How someone can steal our identity in the internet?
The most common methods of online identity theft are as follows.
I. Phishing
In this tactic, hackers send emails to random or specific individuals with the purpose of tricking recipients to perform an action.Basically, they trick the recipients to open a file which usually contains some type of malware. When user enters his/her personal information, it falls straightly into the hands of the attacker. Then the stolen information will be misused.
II. Hacking
Hackers exploit vulnerabilities in your security systems and gain access to personal information. They can perform this task by directly hacking your mobile phone, computer or obtain access to devices by hacking the network you logged into.
III. Malware
Here an attacker infects some malicious software into your devices. When that software is executed, the attacker will gain access to your personal information in devices.
IV. Remote Access
In this method, the attacker tries to trick you by mentioning that there are some issues with your computer and/or network and they navigate you to buy a third-party software to fix those issues. This software will contain malware or severe security vulnerabilities.
V. Skimming
In this method, attackers steal your credit or bank card details. First of all, they configure an ATM machine to read your card information when you withdraw money. Then the stolen information will be transferred into a storage device of the attacker. They will misuse those details to make online purchases, withdraw money etc.
Some Real-life Examples for Online Identity Theft
- A person called Phillip Cummings left his job in one of the software companies of US. He was working as a help desk worker and he had access to logins and passwords of 33000 credit reports. Monetary of that breach was between 50-100 million dollars.
- David Jackson and Lara Love who lived in Santa Cruz County in California, were tapping into a neighbor’s wireless internet router. They were able to access private data via that connection. After that neighbors realized they were having some bank accounts that they had never opened. Lara & David faced 24 years in state prison due to this crime.
- An 82 years old women from Lewisville, North Carolina got an email from a hacker that represented himself as “PayPal” support. He made a similar email account and asked for some personal data.
- As majority of drivers, Sadie Cornelius (US) used her debit card in a gas station. Owners of that card reader configured it to make a carbon copy of the magnetic strip. They managed it to a fake card and misused it. Ultimately, she realized that all of her money was taken by someone in Alexandria. Then she was able to contact the bank and change pins and passwords.
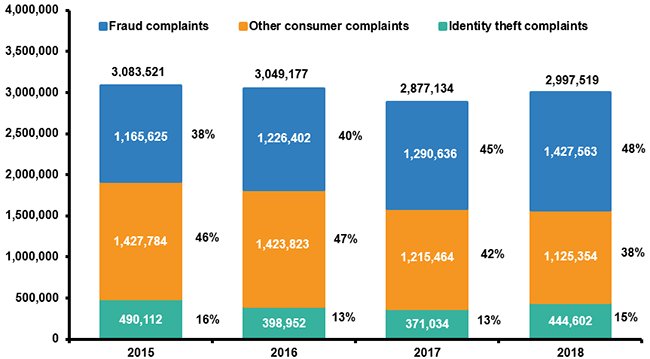
This graph shows the details of reported top cyber crimes from 2015 to 2018. Identity theft is fallen under 3rd place in all those years.
How to Stay Safe?
When your online identity is stolen by attackers, damage level depends on the purpose of attackers and our safety plans for such attack. For some cases it will be easy to recover and at the same time it can be frustrated and difficult to overcome the more extreme forms of attacks. Even though each scam type has its own way of protection, as users, you need to be aware of some common safety methods.
I. Activate security freezes and fraud alerts.
When an attack has happened, it’s really important to have rapid reactions. Security Freezes play a major role in that scenario. This will limit the access of your credit reports only for the bank andsome government agencies. If someone else is trying to access those data, you’ll get a security alert.
II. Use Antivirus & Anti-Malware Software
This can be considered as one of the basic steps of protecting your online identity. You will be able to overcome most of hacking attempts and malware by enabling these programs. Anti-malware will serve as an extra layer of protection in case of failed scenario of antivirus.
III. Protect Ourselves on Social Media.
This is one of the main reasons to become a victim of an identity thief. Today it has become a trend of expressing too much personal information on social media. That can be the easiest way of losing your identity. You have to make sure that you publish only selected information which will not cause damage in any way. At the same time, it’s better if you can set your accounts to private mode so only friends can see your posts and other information.
IV. Hide the PIN when using ATMs.
When you withdraw cash from an ATM machine, someone can be there, watching your inputs to the machine with the help of a small camera or just by looking over your shoulder. Hence, you have to make sure they won’t see your PIN.
V. Use Strong & Unique Passwords.
This plays
a major role when protecting our online identity. Most of people tend to use a
simple password for their convenience to remember it and most of the times they
use their names, nick names or telephone numbers for passwords. These things
can be easily guessed by an attacker. And you should never reuse passwords
between different accounts. Some times it’s impossible to remember different
passwords for accounts but there are some online tools such as “LastPass…”
(https://www.lastpass.com/password-generator) to store our passwords and
usernames in a safe environment.
VI. Don't click on Unauthorized Links
If there are suspicious emails, we should not open those. If we accidentally open such a suspicious email, we should not click on any attachments or links.
Conclusion
Among various kinds of cyber-attacks, identity theft is a real threat and there is a high probability of falling victims to online identity theft. First of all, we have to be smart while using the internet and we should stick to the common safety methods in order to prevent such attacks. We should not be late to take proper reactions when we realize we are a victim of an attack otherwise the damage could be worse.
References
[1] Chris Hauk, “Privacy Advocate for Pixel Privacy” [Online] Available at: https://pixelprivacy.com/resources/online-identity-theft/ [Accessed 22 March 2020].[2] CNBC contributor HERB WEISBAUM, “Seven signs you’re a victim of identity theft” [Online] Available at: https://www.cnbc.com/2014/01/17/seven-signs-youre-a-victim-of-identity-theft.html [Accessed 23 March 2020].
Prageeth BhanukaDepartment of Computer EngineeringFaculty of Engineering University of Sri Jayewardenepura




No comments:
Post a Comment